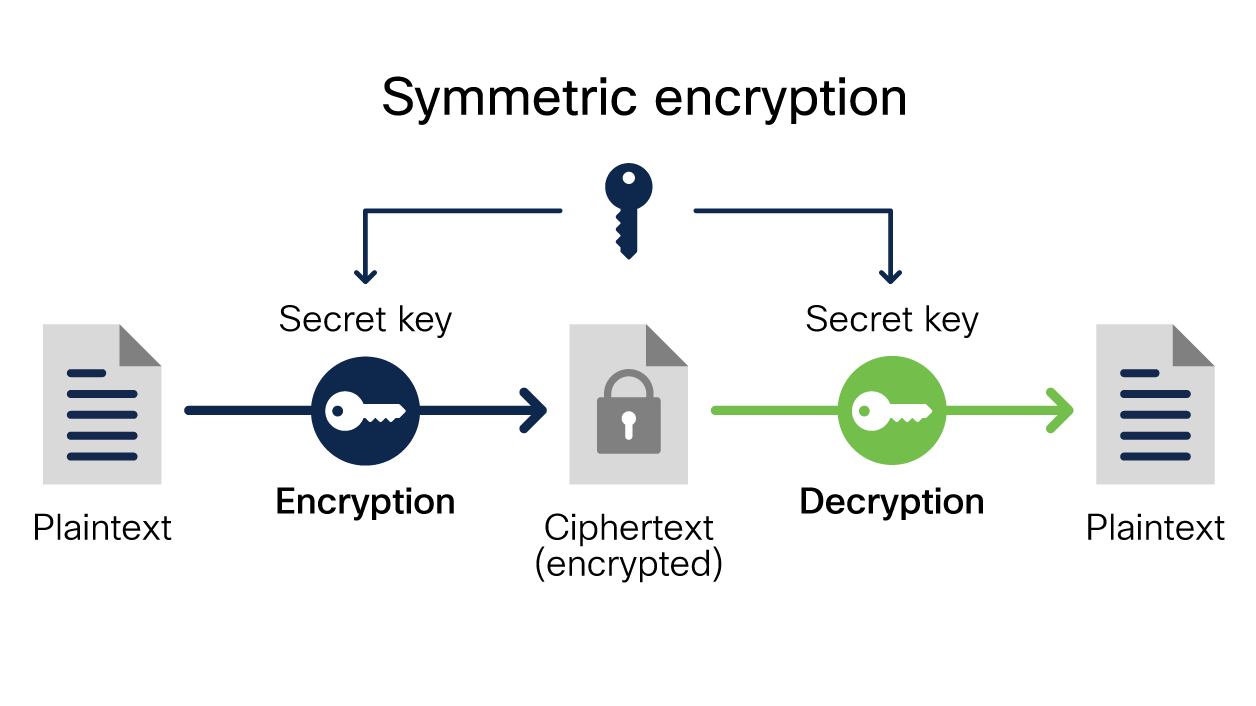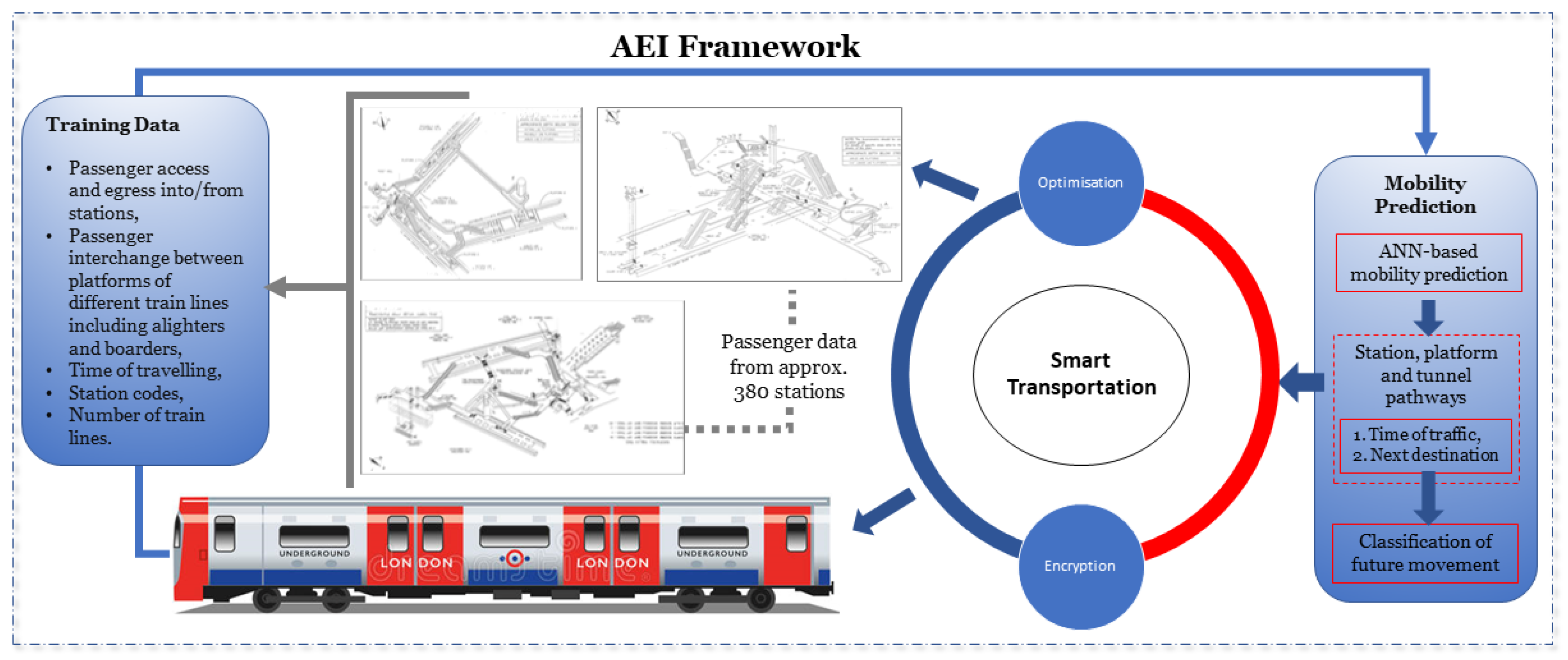
Sensors | Free Full-Text | Mobility Prediction-Based Optimisation and Encryption of Passenger Traffic-Flows Using Machine Learning

15th Plenary Meeting of the European Judicial Cybercrime Network | Eurojust | European Union Agency for Criminal Justice Cooperation

19 Security Awareness Statistics You Should Know Before Offering Training - Hashed Out by The SSL Store™

CISociologíaEducació on X: "3rd International Workshop on Time Studies in Childhood and Youth de la Universidad de Valencia (UV) 2 y 3 diciembre 2021 Program & Registration https://t.co/r0YtwkbaQD https://t.co/ttWQk45ZKS https://t.co/IV0xsHsMb4" / X
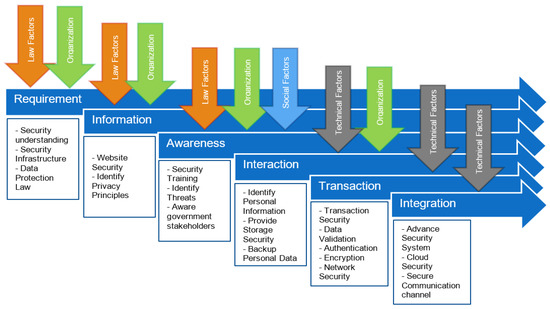
Applied Sciences | Free Full-Text | Evaluating a Proposed E-Government Stage Model in Terms of Personal Data Protection

Pragmatic solutions to reduce the global burden of stroke: a World Stroke Organization–Lancet Neurology Commission - The Lancet Neurology